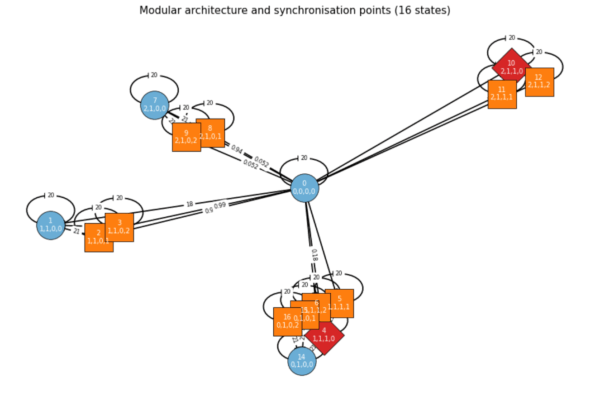
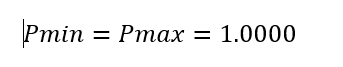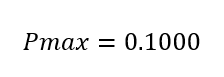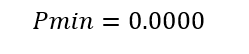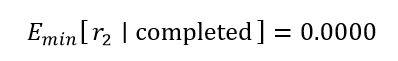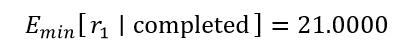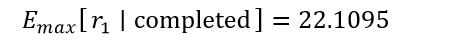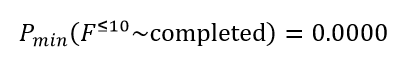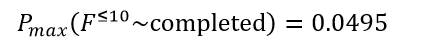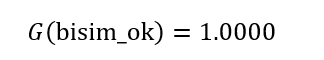1. All controller–pilot, avionics, and supervisory interactions from the requirements capture procedure led to a 358-state Markov decision process (MDP) that precisely models the probabilistic timed automaton. The global timer t used twenty-tick cycles to represent real-time deadlines through a one-and-a-half-second tick duration (see Figure 1).
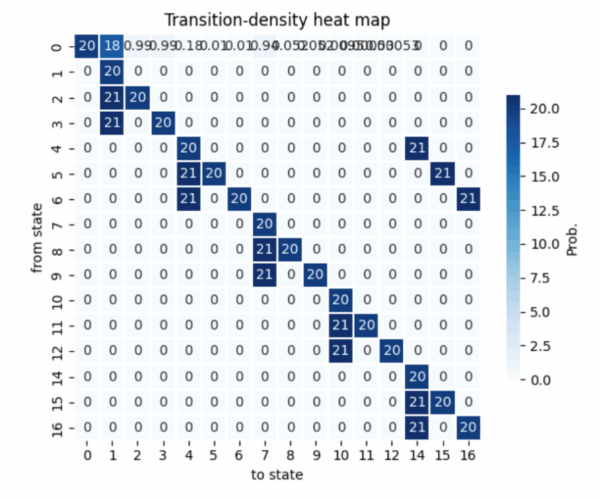
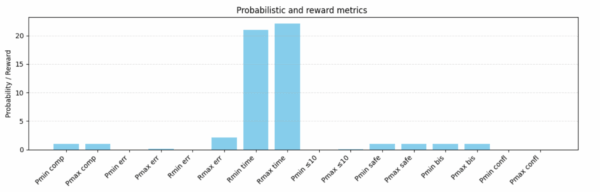
2. The composed MDP underwent breadth-first exploration which achieved convergence at 23 iterations to reveal 946 probabilistic transitions. The Bellman equations received value-iteration solutions for reachability and reward expectations which achieved a residual below to confirm numerical soundness for both pessimistic and optimistic scheduler resolutions.
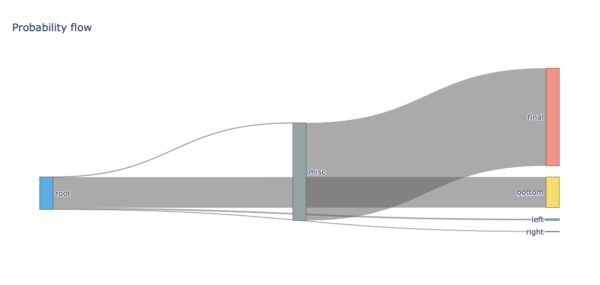
3. A total of sixteen PTCTL properties underwent evaluation. Any adversarial or cooperative scheduling policy leads to inevitable mission termination because unconditional reachability of the terminal label (“completed”) proved both